Reality Cloud Studio
Security and Compliance
Selected Security Policies and Procedures
Data Privacy
Data Privacy
Product Security
Product Security
Commitment to Transparency
Commitment to Transparency
Continuous Improvement
Continuous Improvement
Personal Data Protection
Personal data is protected and retained in compliance with Hexagon’s Data Protection Program, which is based on GDPR, while taking local privacy laws into account worldwide. The Hexagon Privacy Notice can he found here: Privacy Notice | Hexagon
- Data Collection and Use: Hexagon collects personal data only for specific, legitimate purposes and ensures it is used in accordance with applicable laws.
- Security Measures: Hexagon implements technical and organizational measures to safeguard personal data against unauthorized access, alteration, or destruction.
- Data Retention: Personal data is retained only as long as necessary to fulfill the purposes for which it was collected or as required by law.
- User Rights: Individuals have rights regarding their personal data, including access, correction, deletion, and restriction of processing.
- Third-Party Sharing: Personal data may be shared with third parties only under strict conditions and with appropriate safeguards in place. Hexagon only shares personal data with third parties that support us in the implementation, operation, or support of the platform. Encryption and pseudonymization are used to avoid identification of data subjects. Access to personal data is restricted on as needed basis. All third parties have committed to personal data protection of the data they get access to.
Encryption
We ensure that our databases, your uploaded content as well as the communication thereof are protected with industry-leading security measures that safeguard your data
Hexagon meets industry standards and regulatory requirements for data protection. It provides multiple layers of protection, ensuring that our data is secure both at rest and in transit.
Supplier Management
Hexagon prioritizes suppliers who adhere to industry-leading security standards and best practices. This includes robust encryption, regular security audits, and comprehensive risk management strategies.
We require that external suppliers that process Customer Content or that are critical for availability of the platform to have an ISO27001 or a SOC2 Type2 certification. We require that external suppliers that process personal data commit to protection of that personal data. We only select external suppliers whose platforms support encrypted communication.
Cloud Hosting
Reality Cloud Studio is a Hexagon-delivered Software as a Service offering hosted entirely in Amazon Web Services (AWS), developed exclusively by Hexagon.
A mature cloud provider, AWS, has been selected for its exceptional scalability and stability and ability to conform to ISO and SOC2 compliance standards.
User-uploaded data is stored in the AWS data center located within the country in which they register their account or the nearest possible data center if one is not available within their country.
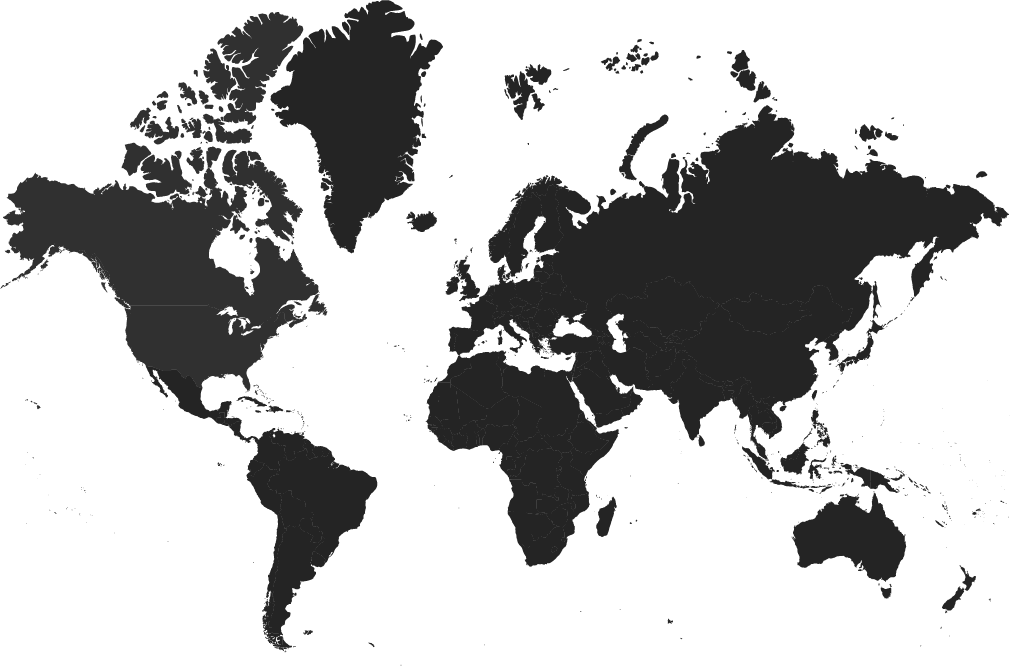
Oregon
Ireland
UAE
Canada
Data Segregation
Reality Cloud Studio segregates instance metadata from customer files to minimize the risk of unauthorized access to sensitive information. This separation ensures that metadata, which may contain operational details, does not expose customer data.
Customer files are stored in a siloed fashion within AWS ensuring isolation and security of each customer’s confidential files and personal data.
Software Development
Reality Cloud Studio conforms to a well-defined software lifecycle development policy following best practices and ensuring proper change management, design & development, maintenance, and business continuity procedures are in place.
Environment Segregation
Reality Cloud Studio employs a multi-tenant system for segregating unique environments and instances of Reality Cloud Studio. Unique tenants are deployed for development, QA, UAT and Production environments that minimize the risk of unauthorized access and potential security breaches to maintain the stability of our production systems.
Code Review and Testing
Reality Cloud Studio adheres to a strict code review process requiring all code to pass through a code review process, automated testing, manual testing and product management approval before being exposed publicly. Code reviews help identify security vulnerabilities and ensure that secure coding practices are followed. This enhances the overall security of Reality Cloud Studio.
Penetration and Vulnerability Testing
Reality Cloud Studio performs vulnerability scans to ensure that potential vulnerabilities are immediately identified. The patch management program ensures that available patches are applied throughout the platform and its applications according to criticality.
Reality Cloud Studio implements regular penetration testing, enabling us to continuously challenge and improve our security posture. This dynamic process helps us adapt to evolving threats and maintain robust defenses
HR policies
To ensure the highest level of security across our organization, we require all employees to complete comprehensive security and compliance trainings on a regular basis.
Access Reviews
Reality Cloud Studio conducts regular access reviews of both the platform and development environment to ensure only necessary and authorized people have access to our systems, data and code.
Employee devices
Hexagon requires employee devices to adhere to corporate security measures including data encryption requirements, Operating system security updates and patches, endpoint protection via anti-virus, anti-malware and firewall software and multi-factor authentication.
Physical Security
Offices and their IT networks ; all facilities maintain tight access control measures, security systems and visitor management policies.
Business Continuity and Disaster Recovery
Our Business Continuity and Disaster Recovery strategy ensures that we are prepared to respond effectively to any disruption. Our Strategy encompasses five key tenants.
- Proactive Planning: We develop and maintain detailed continuity and recovery plans that outline the steps to be taken in the event of various types of disruptions. These plans are reviewed and updated to address emerging risks and changes in our operations.
- Risk Assessment: We conduct thorough risk assessments to identify potential threats to our operations and prioritize our response efforts. This proactive approach helps us mitigate risks and minimize the impact of disruptions.
- Redundancy and Resilience: We invest in redundant systems and infrastructure to ensure that critical functions can continue without interruption.
- Data Protection: Our disaster recovery strategy includes robust data backup and recovery processes. We ensure that your and our data is regularly backed up and securely stored with our infrastructure suppliers, allowing for quick restoration in the event of data corruption or data loss.
- Testing: We test our continuity and recovery plans and ensure their effectiveness. These exercises help us identify areas for improvement and ensure that our response teams are well-prepared.
User Management
User Authentication
Reality Cloud Studio includes native authentication functionality based on widely used authentication standards.
Portal Access Rights
Users may only be granted access to a customer portal via direct invitation by an admin or maintainer. Once invited, users may register an account with access only to the limited information that the invitation issuer permits. Users may downgrade their own permission level but never upgrade it.
Portal access rights define what type of actions a user can execute within the platform such as the creation of projects, upload of data, invitation of new members and more. For a complete list of Portal access roles and permissions, please visit Reality Cloud Studio User Administration and Authorization Concept (leica-geosystems.com).
Multi-tiered project and asset permissions
Reality Cloud Studio uses a multi-tiered permission structure with Portal and per-project access rights. Employee and Member users may be granted or denied access to specific projects and prevented from making new projects or uploading data. This granularity of access provides enhanced security to reduce the risk of unauthorized access to projects or consumption of paid features. For a complete list of Project access roles and permissions, please visit Reality Cloud Studio User Administration and Authorization Concept (leica-geosystems.com).
Compliance and Certification
ISO/IEC 27001
Reality Cloud Studio is in scope of the ISO27001:2022 certificate of the HxDR platform. ISO/IEC 27001 is the world’s best-known standard for information security management systems (ISMS). Conformity with ISO/IEC 27001 means that an organization or business has put in place a system to manage risks related to the security of data owned or handled by the company, and that this system respects all the best practices and principles enshrined in this International Standard.
Soc 2 Type II
Reality Cloud Studio has achieved SOC 2 Type II certification which demonstrates the product’s commitment to maintaining high standards of data security and privacy, providing assurance to clients and stakeholders that their data is handled with the utmost care and integrity. SOC 2 Type II Certification is a rigorous auditing process that evaluates the operational effectiveness of a company’s systems and controls over a specified period. Developed by the American Institute of Certified Public Accountants (AICPA), this certification focuses on five key Trust Service Criteria: security, availability, processing integrity, confidentiality, and privacy.
GDPR
The Hexagon Data Protection Program is based on and compliant with GDPR. The General Data Protection Regulation (GDPR) is a comprehensive data privacy law enacted by the European Union (EU) that came into effect on May 25, 2018. It sets strict guidelines for the collection, processing, storage, and transfer of personal data of individuals within the EU. Reality Cloud Studio meets or exceeds the requirements of GDPR for customer privacy.
CCPA
Whereas the Hexagon Data Protection Program is based on GDPR, it is extended and overruled by local laws and regulations where required. As such it is also compliant to CCPA. The California Consumer Privacy Act (CCPA) is a landmark privacy law that was enacted in 2018 to enhance privacy rights and consumer protection for residents of California. It defines the rights of residents of the state to request copies of the personal information a company collects on them, right to delete that information and the right to Opt-out of the sharing of their personal information. Reality Cloud Studio meets or exceeds the requirements of CCPA for customer privacy.